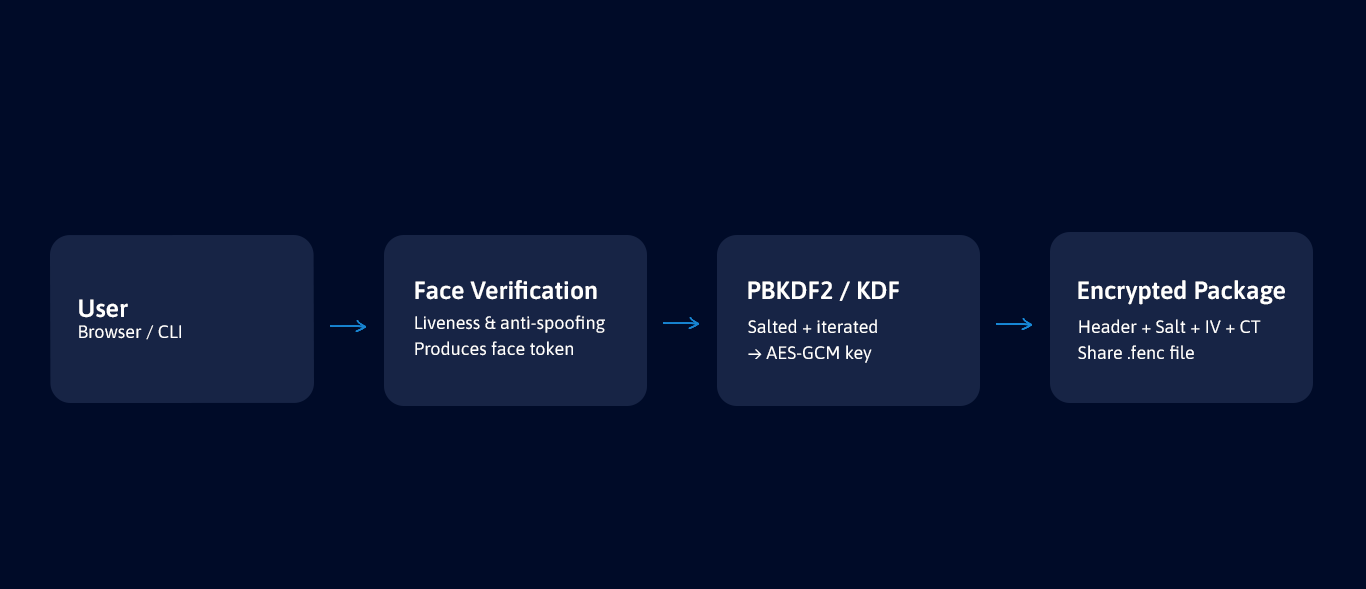
Lock documents, photos, and videos to a face.
Encrypt files locally in your browser and bind access to verified identity. Only the right face can decrypt—no passwords, no OTPs.
Demo simulates face matching. Replace with Axiam's biometric SDK for production.
Encrypt with Face
Choose any document, photo, or video. Output is a single
.facelock container.
Decrypt with Face
Use the same face photo used at enrollment to unlock the encrypted file.