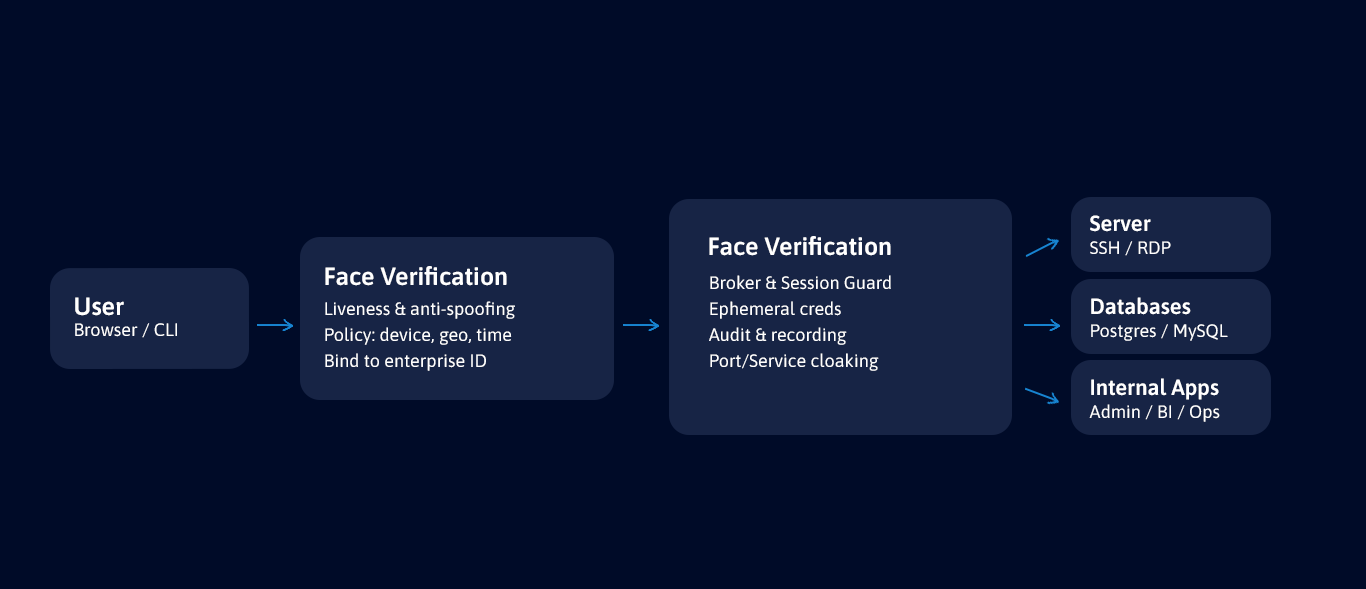
Only the right face gets in.
A single, secure gateway that verifies real identity before any port opens. No passwords to steal, no OTPs to phish—just verified access to the resources you choose.
* Demo simulates the flow; you have to integrate with Axiam's biometric SDK for production.
No real camera or biometrics used